GnuPG and PGP
Basic Information about GnuPG and PGP
Introduction
Each RegAcc must record at least one key with DENIC.
What is GnuPG / PGP?
PGP (Pretty Good Privacy) / GnuPG (an Open Source / Open PGP Implementation) are programs which make it possible to sign and encrypt e-mails, texts and files. It is a technique considered to offer a very high level of security and thus to permit secure communication between two parties.
Supported Versions
DENIC supports all versions of GnuPG and PGP.
What Is Meant by Keys and how Are they Structured?
A key is always comprised of two parts:
- the public key and
- the private key.
As you will realize, this encryption procedure is an asymmetrical one. So each user has two keys which belong together, the private one and the public one. GnuPG/PGP generates a so-called hash value (secret key) out of the selected password. The hash value or secret key, in turn, is used to generate the private part of the key.
Two of the things you can do with your private key are to sign messages and decrypt them.
The public key can be used to verify messages and encrypt them.
Each key contains various items of information, such as:
| Length | The length of the key, for example 2048 bits |
| Type | For example: DSA and ElGamal |
| KeyID | The key’s unique identifier, for example: 0x00F555A |
| Date of creation | Dates are written: yyyy-mm-dd |
| Name | For example: DENIC-1000002 Communication Key for Production |
| For example: example@denic.de | |
| Fingerprint | The key’s "fingerprint", which permits unique identification in combination with the KeyID |
| Expire | The date on which the key will expire, if stated |
Let us take an example key:
|
In this example:
- Length: 2048 Bit
- Type: DSA (symbolized by the "D" in 2048D; if RSA keys were used, it would be for example 2048R)
- KeyID: 0xF81AE61F
-
Created on: 2001-12-11 (ISO format for dates: YYYY-MM-DD)
- Name: Business Services
- E-mail: example@denic.de
- Fingerprint: 4943 3AA7 6A85 306E 23A4 A1AC D4B9 6CF6 F81A E61F
- Expire: The key expires 2002-12-11
GnuPG / PGP save keys in a file or set of files known as a "keyring".
Usually, a keyring is comprised of two files: "pubring.pkr" and "secring.pkr" (for PGP) or "pubring.gpg" and "secring.gpg" in $HOME/.gnupg/ (for GnuPG).
Master and Communication Keys
DENIC differentiates between two types of keys:
- master key
- communication key
The master key is needed to
- sign e-mails to request access to the Registrar Administration Interface (RAI) at DENIC Business Services
- authorize changes to the stored RAI info e-mail address to which DENIC sends notifications about changes to the RegAcc profile
- authorize additional orders of RegAccs/contingents
- authorize the creation of accesses to the member websites
The master key or the communication key is needed to
- communicate between members and DENIC via e-mail on general topics
Function and requirements of the master key and communication key
The key is used for authorization and identification vis-à-vis DENIC when processing orders and other e-mail communication. Each RegAcc must store at least one key.
- Each key must be unique. A key that has already been used cannot be reused.
- The number of keys allowed is not limited.
- All keys must have a validity period of no more than 731 days. After the validity period has expired, the key is deleted from DENIC's keyring and can no longer be used.
- DH/DSS, RSA, DSA or DSA and Elgamal must be selected as the key type.
- The key length must be at least 2048 bits.
- The signature algorithms permitted for requests are:
- RIPEMD160withRSA
- RIPEMD160withECDSA
- RIPEMD256withRSA
- SHA256withDSA
- SHA256withECDSA
- SHA384withDSA
- SHA384withECDSA
- SHA512withDSA
- SHA512withECDSA
- SHA256withRSA
- SHA384withRSA
- SHA512withRSA
- Each key should be labeled with a secure passphrase.
- DENIC recommends choosing a unique name for each key, consisting of RegAccId, RegAccName and, if applicable, the purpose of use.
- Example: DENIC-99995 DENIC eG.
Activating a Key
A new key can be managed via RAI. The key will be active within 5 minutes after being inserted.
Expire of a Key
Expired keys will be removed from the DENIC keyring and will no longer be displayed in RAI.
Deleting a Key
If you wish to remove a key from the DENIC keying (e.g. because the key has been compromised), you can remove it from the DENIC keying at any time using the RAI.
Step by Step: Creating a Key with PGP
These instructions are based on the PGP version 9.9.1.
- Start the PGP-Desktop.
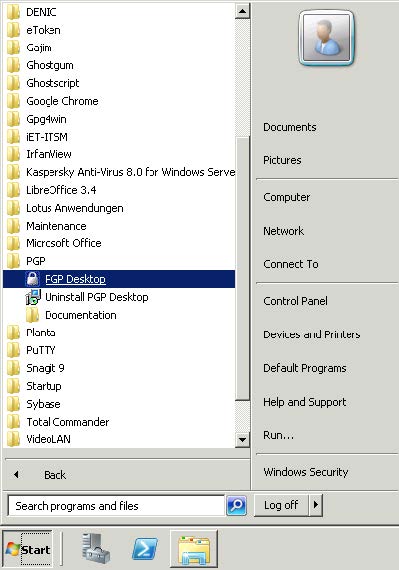
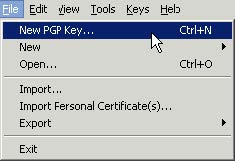
- Select New PGP Key in the File menu
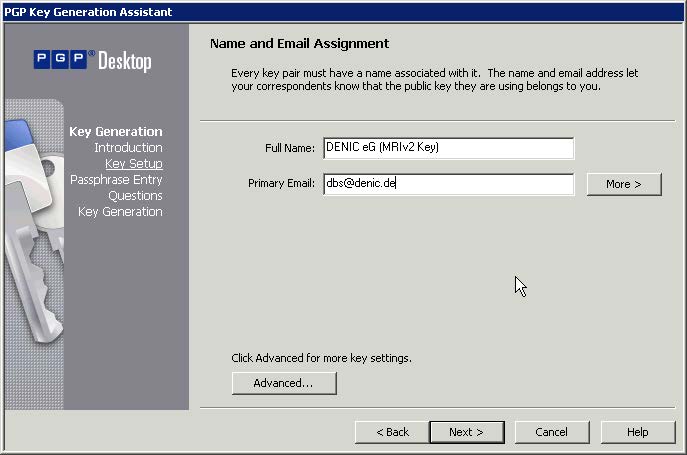
- Enter the name of the person / role who is going to use the key and the associated e-mail address
- Click "Advanced"
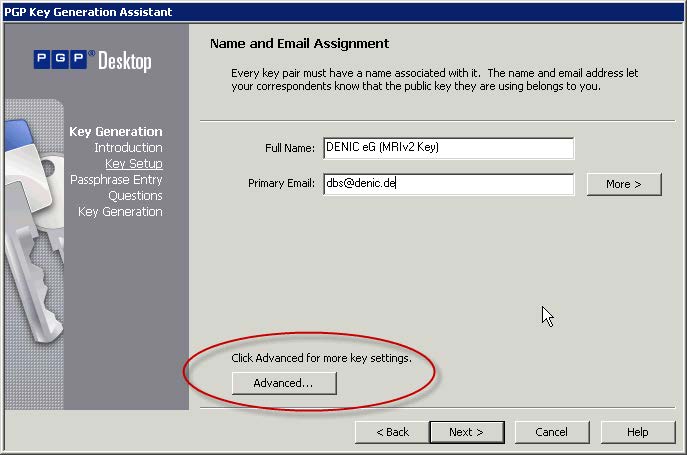
- Check whether the value displayed for the key size is at least "2048"
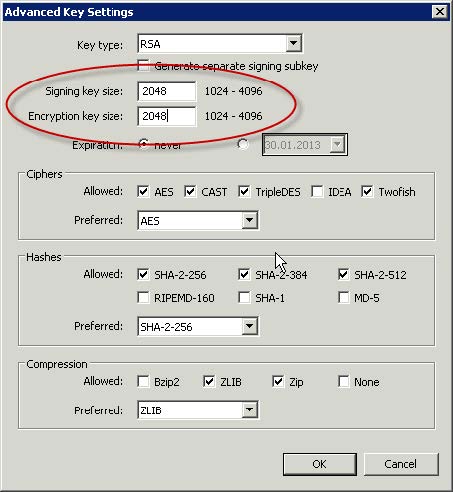
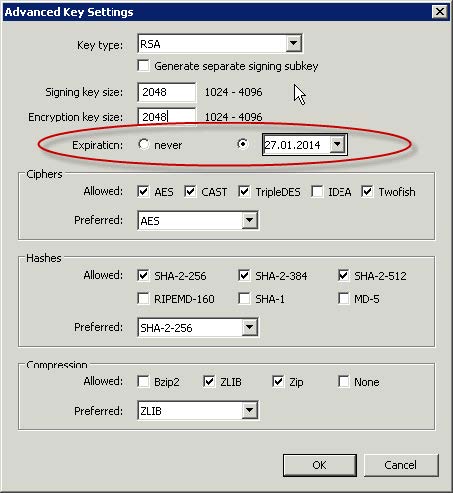
- For the expire date click the date field and enter a date that is no more than 731 days in the future
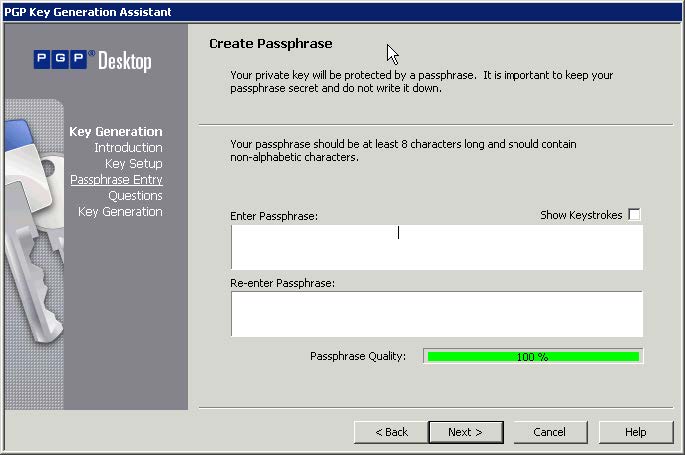
- Click "OK" and "Next" and enter a secure passphrase
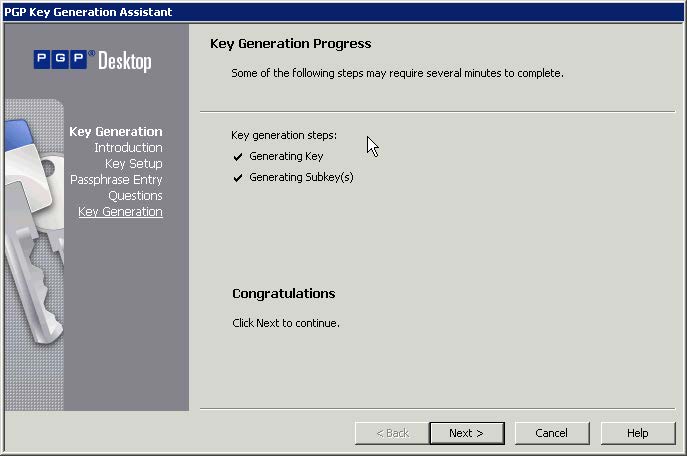
- Click "Next" and your pair of keys is generated
- After that, you have the option of uploading your key to a public keyserver if you wish.
- Then right-click on your key
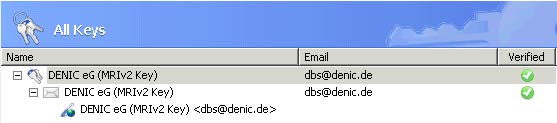
- Wählen Sie "Exportieren" aus.
- Select where to store the key file and make sure that you have NOT selected "Include Private Key(s)"!
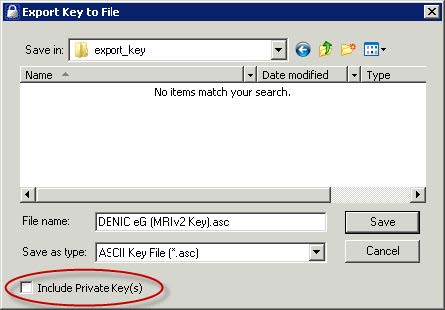
- Save the created key in a save location.
- Then right-click on your key
| Notice |
Please note that the key file also contains the private key. Store the private key carefully as it will be used for signing. |
Incorporating the Communication Key via the Registrar Administration Interface
- New communication keys can be managed via RAI.
- Detailed information on this topic can be found in the documentation "RAI - Registrar Administration Interface", How to Edit the RegAcc Profile, "PGPKey".
- Open the key file with a text editor.
- Select and copy only the public part of the key.
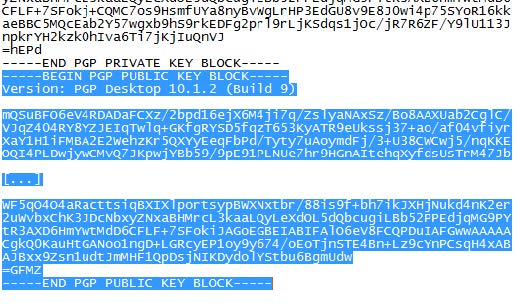
- Insert the text block in RAI under PGPKey and save your action.
| Notice | Now you can use the key within 5 minutes. |
Step by Step - Creating a Key with GnuPG
Creating a Key
These instructions are based on GnuPG, version 1.4.7. Follow the procedure described below to create a key:
Linux
- Start a computer console (by pressing ALT+F2 and enter "konsole" under KDE and "gnome-terminal" under GNOME).
Windows
- Open a command window (Start -> Run -> cmd)
- Type in "gpg --gen-key"
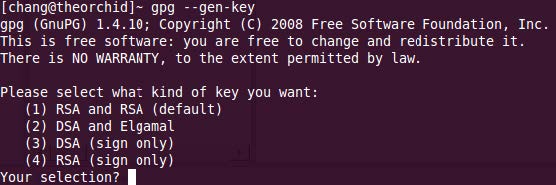
- Now select what kind of key you want (DENIC recommends to select either "RSA and RSA (default)" or "DSA and Elgamal").
- Now enter the key size. Please enter at least 2048 but no more than 4096 bit.
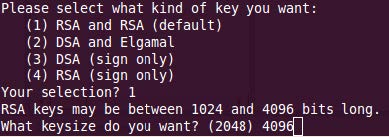
- Specify how long the key should be valid:
- You may state the term of validity for the key in days (Enter, for example, 10 for 10 days) or
- in weeks (Enter, for example 4w for 4 weeks) or
- in months (Enter, for example, 12m for 12 months) or
- in years (Enter, for example, 2y for 2 years)
Notice DENIC recommends to enter the maximum validity of 2years.
- Bestätigen Sie im Anschluss Ihre Eingabe.
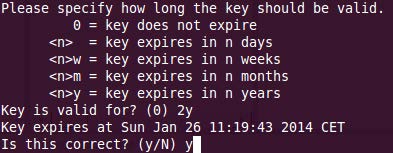
- Enter the name of the person / role who is going to use the key and the associated e-mail address
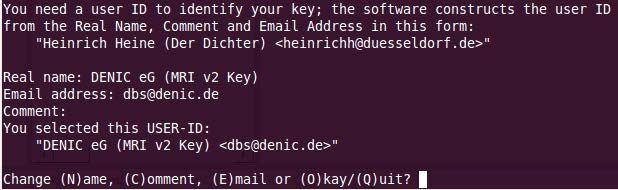
- Confirm your entry again
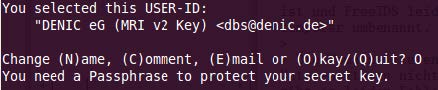
- Enter a secure passphrase. Now your key is generated
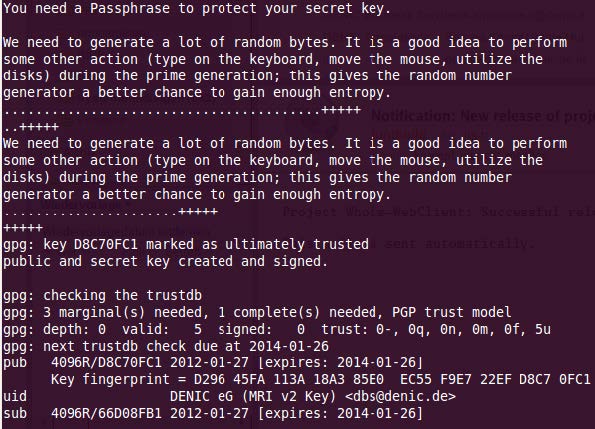
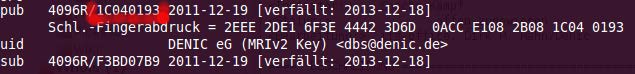
- You may now export your key by typing in gpg -a --export <KeyID> > mykey.asc. You will fin the key ID in the pub line at the top
- Please also export the private key with gpg-a – export-secret-keys<KeyID> >mysecretkey.asc.
- To conclude the action, please save your pair of keys in a save location.
| Notice |
Please note that the key file contains the private key. Be careful to store the private part in a secure place, since it is used for signing. |
Incorporating the Communication Key via the Registrar Administration Interface
- New communication keys can be managed via RAI.
- Detailed information on this topic can be found in the documentation "RAI - Registrar Administration Interface", How to Edit the RegAcc Profile, "PGPKey".
- Open the key file with a text editor.
- Select and copy only the public part of the key.

- Insert the text block in RAI under PGPKey and save your action.
| Notice | Now you can use the key within 5 minutes. |
Further Information About GnuPG / PGP
List of important GnuPG commands
| -s, --sign | Create signature |
| --clearsign | Create cleartext signature |
| -e, --encrypt | Encrypt file / e-mail |
| --decrypt [file] | Decrypt file |
| --verify [signature] [file] | Verify signature |
| --list-keys | List all keys |
| --list-public-keys | List all public keys |
| --list-secrect-keys | List all private keys |
| --list-sigs | List all keys with their signatures |
| --check-sigs | Like --list-sigs, but including verification of signature |
| --fingerprint | Like --list-keys, but including output of fingerprint |
| --gen-key | Delete key from keyring |
| --delete-key | Schlüssel aus dem Keyring entfernen |
| --delete-secret-key | Delete public and private key from keyring |
| --export [KeyID] | Export public key |
| --export-secret-keys [KeyID] | Export private key |
| --import | Import public key into keyring |
| -a, --armor | Output in"ASCII-armor" |
| -o, --output [file] | Transfer output to file |
| -o [file] –a –export [KeyID] | Output public key in form of ASCII-armor in file |
RFCs relating to GnuPG / PGP
| RFC1321 | The MD5 Message-Digest Algorithm |
| RFC2104 | HMAC: Keyed-Hashing for Message Authentication |
| RFC3156 | MIME Security with OpenPGP |
| RFC4880 | OpenPGP Message Format |